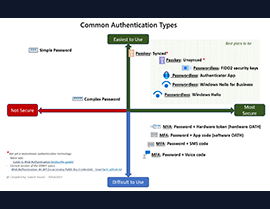
 In the cybersecurity realm, strong authentication methods are not just a recommendation; they are a necessity. They ensure that only authorized users access sensitive information, maintaining the integrity of your digital assets. However, the real challenge lies in striking the perfect balance between robust security, user-friendly usability, and consistent availability. This delicate balancing act is crucial in designing effective authentication systems. Optimal solutions should be strong enough to ward off unauthorized access, yet intuitive and accessible for legitimate users. The goal is to position yourself in the upper-right quadrant, where all three factors—Usability, Availability, and Security—meet optimally. This LinkedIn post invites a crucial discussion: what authentication methods are you currently using, and how do they measure up against these parameters? Join the conversation to explore the best practices and share insights on achieving this equilibrium in authentication strategies.
In the cybersecurity realm, strong authentication methods are not just a recommendation; they are a necessity. They ensure that only authorized users access sensitive information, maintaining the integrity of your digital assets. However, the real challenge lies in striking the perfect balance between robust security, user-friendly usability, and consistent availability. This delicate balancing act is crucial in designing effective authentication systems. Optimal solutions should be strong enough to ward off unauthorized access, yet intuitive and accessible for legitimate users. The goal is to position yourself in the upper-right quadrant, where all three factors—Usability, Availability, and Security—meet optimally. This LinkedIn post invites a crucial discussion: what authentication methods are you currently using, and how do they measure up against these parameters? Join the conversation to explore the best practices and share insights on achieving this equilibrium in authentication strategies.